|
|
楼主 |
发表于 2022-12-5 11:27
|
显示全部楼层
看下这个:https://help.mikrotik.com/docs/d ... et+Flow+in+RouterOS
还有这个:https://doc.opensuse.org/documen ... urity.firewall.html
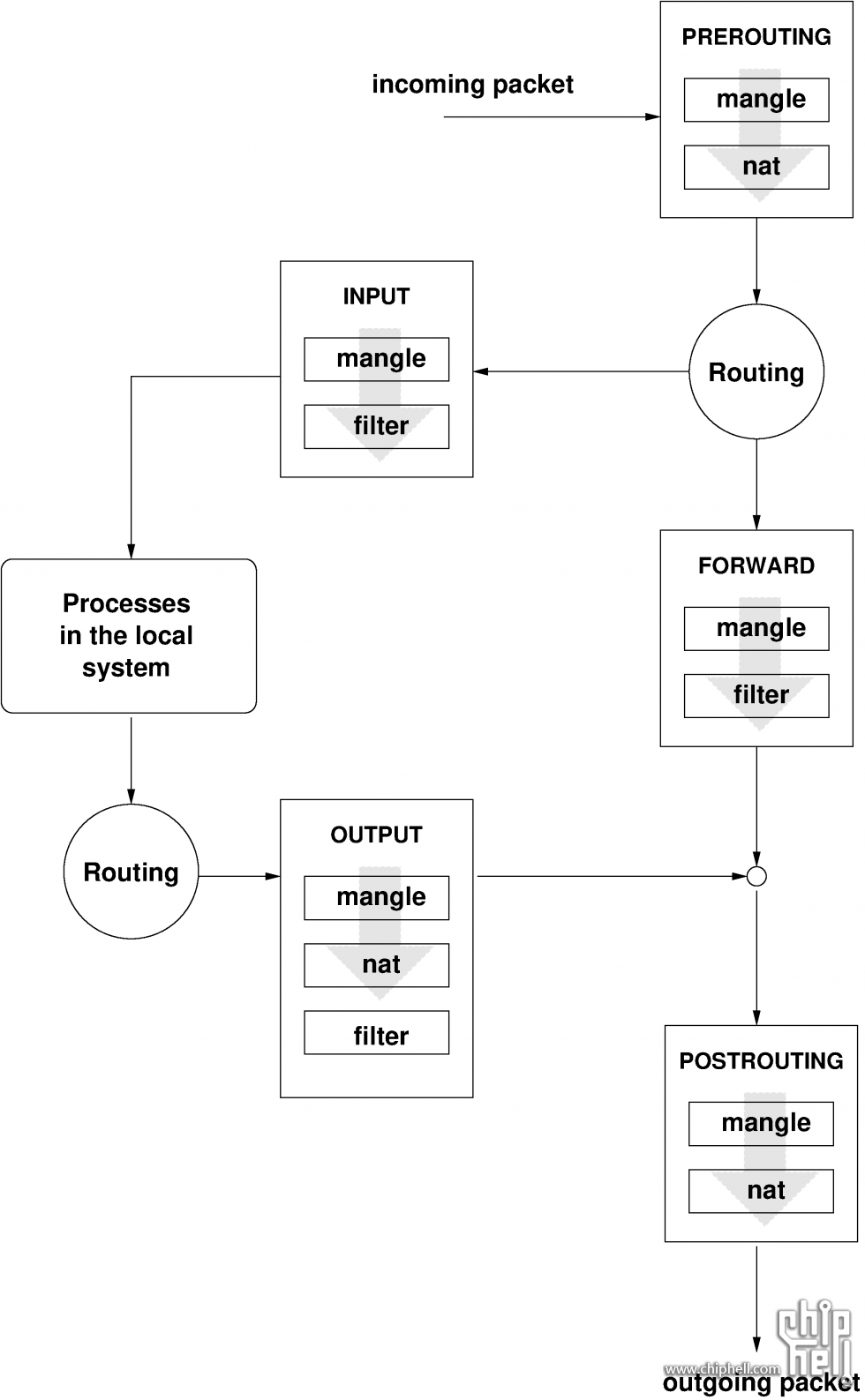
In the simplest case, an incoming packet destined for the system itself arrives at the eth0 interface.
The packet is first referred to the PREROUTING chain of the mangle table then to the PREROUTING chain of the nat table.
The following step, concerning the routing of the packet, determines that the actual target of the packet is a process of the system itself.
After passing the INPUT chains of the mangle and the filter table, the packet finally reaches its target, provided that the rules of the filter table allow this.
Masquerading is the Linux-specific form of NAT (network address translation) and can be used to connect a small LAN with the Internet. LAN hosts use IP addresses from the private range and on the Internet official IP addresses are used.
To be able to connect to the Internet, a LAN host's private address is translated to an official one.
This is done on the router, which acts as the gateway between the LAN and the Internet.
The underlying principle is a simple one: The router has more than one network interface, typically a network card and a separate interface connecting with the Internet.
While the latter links the router with the outside world, one or several others link it with the LAN hosts. With these hosts in the local network connected to the network card (such as eth0) of the router, they can send any packets not destined for the local network to their default gateway or router.
As mentioned, whenever one of the LAN hosts sends a packet destined for an Internet address, it goes to the default router.
|
|
 310112100042806
310112100042806
